CD Tower and Virtual CD Tower
Virtual CD/DVD Server
NAS
Networking
Legal Research Programs
Glossary
Downloads
Search
Email Us
Tel.: 800-385-6442
Fax: 781-279-4262
©2001 Academy Computer Services, Inc.
All rights reserved.
Terms & Conditions
Networking
Peer to Peer
NICs
A Network Interface Card is the circuit-board "thingy" that is inserted into your computer and acts as the gateway between the computer and the rest of the network. Some new computers arrive with a NIC already installed. Some have a NIC integrated into the motherboard of the computer. Most computers sold to home consumers do not have a NIC preinstalled. Most computers sold to businesses do. Every piece of computer equipment that has a NIC inside it is a network device. Computers can have NICs. Printers, scanners and fax machines can have NICs.
The most significant thing about the NIC is the speed with which it can send and recieve data. Most NICs are rated for 10BaseT, 100BaseT, or 10/100 Auto Sensing.
| The speed rating | What it means |
| 10BaseT | 10 Mbps Baseband Twisted pair. This rating means that 10 megabits per second are transfered via a base (the cable) that only carries Ethernet traffic, and the wire is made of twisted pairs of wires. To help you understand how fast 10Mbps is; a floppy transfers data at 5 or 6 Mbps. |
| 100BaseT | This can send/recieve data at 100Mbps. Ten times faster than 10BaseT. |
| 10/100 Auto Sensing | The NIC can only function as fast as the hub that its plugged into. An auto-sensing card will detect the speed of the hub and adjust itself to that speed. |
The process for installing a NIC is different for every card. But in general you will need to turn of your computer, open it up, insert the card into a slot on the motherboard, close the computer, and turn it back on. Depending on the type of card you installed, Windows may immediately recognize that a new card has been installed and take you to the "Add new Hardware Wizard". Just follow the bouncing ball to add the driver that lets Windows use the new card.
Wires
UTP![]()
Unshielded Twisted Pair cables are the most common form of network wire. The name refers to how the cable was constructed: there are pairs of wires inside the cable, the two wires in each pair twist around each other, and the pairs are not shielded from each other. This type of wire is frequently called Category 5. Some people just call it Ethernet. That's an awful lot of fancy names for something that looks like a fat telephone wire, so we'll call it by its nickname; Cat5.
Topology
Topology is the the method that the network uses to distribute information. Where you place the computers isn't the topology, although the name leads you to believe that. Even though every computer attaches to a hub, creating a shape that reminds you of a starfish, peer networks actually have a bus topology. A bus works this way.
- Computer1 makes a request that Computer2 send a specific bit of data back to Computer1.
- Computer2 addresses the data to Computer1, but the signal is broadcast to every computer on the network. (Hence the word broadcast. If it was sent to just Computer1 it would be narrowcast.)
- Each computer (Computer1, Computer3, and Computer4) looks at the data "packet" to see who its adressed to.
- Computer3 and Computer4 decide to ignore it because it's not addressed to them.
- Computer1 opens the packet because its addressed to it.
The practical upshot is that there is a lot of traffic on a peer network. Everything is broadcasting; all the time. This can clog things up. Which slows the network response time down. Which is why large networks don't run peer-to-peer; to prevent broadcasting from bringing the network to a screeching halt.
Ethernet
Ethernet is the most common network technology. It was originally developed by Xerox in the 1970s. Ethernet is not the cables you use, you can run Ethernet with a variety of cable types (most of which aren't mentioned here). Instead, Ethernet is the method by which network devices compete for access using Carrier Sense Multiple Access with Collision Detection. Here's how CSMA/CD works.
- There are 4 computers on the network (WS1, WS2, WS3, WS4)
- WS1 makes a request of WS2. "Please send me this data", he says.
- WS2 must divide the data into small pieces to send it through the wire. Each piece is called a data packet, or packet.
- WS2 sends a messge to WS1, "I'm sending the first packet starting now"
- WS2 sends the packet to WS1
- WS2 asks WS1, "Did you get the packet?"
- WS1 responds, "Yes I did."
- WS2 sends a message to WS1, "I'm sending the next packet starting now"
and so on, and so on, and so on.
I bet you're just dying to know why WS2 asks if WS1 got the packet. Because while all this is going on, WS3 and WS4 are talking to each other. Remember that all the data is broadcast, so every computer needs to look at every packet that is sent out onto the network. Lots of packets whizzing by. So many, that it can be difficult for the computer to find a free space to send it packet out into. Kind of like trying to merge a car into highway traffic. And sometimes packets crash into each other. The data packet version of a demolition derby.
When two packets collide, they both disappear. This action is called "dropping a packet" And the only way for WS2 to know if a packet is dropped is to announce that a packet is on its way, and then to ask if it arrived. If the answer is "No", the WS2 resends the packet.
So Carrier Sense Multiple Access with Collision Detection means that multiple devices compete for access to the carrier (the wire) and then must ask to find out if a packet was dropped (collision detection).
Hubs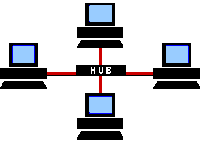
A hub is the center point of a network. Just as the name implies. Every Cat5 cable that is connected to a network device at one end, is connected to the hub at the other end. All information flows through the hub as it passed from one device to another.
Hubs are passive objects. That means that they just let infomation flow through. A hub can't be used to prevent a computer from reaching the World Wide Web. Or to block User1 from accessing User2's computer.
Now that you understand the theory, click here for the next step: physical setup.
